Call 1-314-596-8750 - First 15 minutes FREE
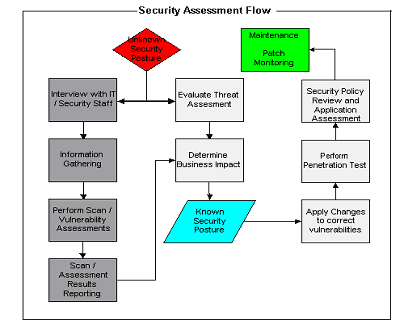
 IT managers spent huge amounts of time and resources to thwart the threat of year 2000 problems back then however most didn't understand that information security breaches in the Internet economy would be an even bigger threat. And unlike the millennium rollover bug, security is not a one-time, easy-to-identify issue. It's a process that must be continually refined using audits, access-rights revisions, new tools, and changes to how data is stored. That may be why so many businesses put security on the back burner until a crisis flares up. Protection from security breaches requires investment in technology, services, and personnel as well as adjustments in corporate culture--now. INTEK has developed a suite of services to address the risks associated with having your systems publicly accessible to the Internet. Our offering is broken down into two components. The first component is performed remotely and consists of a network scan and vulnerability assessment. Prior to the scan, INTEK will need to gather information about your network. Once this phase is complete INTEK will provide a report with the results of our scan. We will also make basic recommendations on how to correct the problems that were identified. Optionally, INTEK consultants would be available for onsite assistance with correcting the vulnerabilities. Once the problems have been addressed the penetration tests and vulnerabilities assessments will be performed to verify the problems detected in the first scan have been corrected. The second component of our services will be performed onsite. It includes reviewing/changing or developing a network security policy. It also addresses the customers current process for keeping operating system and applications patches up to date. The last and most critical phase of our onsite assessment is a systematic way for an organization to address its information security risks, sorting through the complex web of organizational and technological issues. At the core of the approach is the concept of self-direction, where the organization manages and directs the information security risk evaluation. The approach uses a small, interdisciplinary team of an organization's personnel, the analysis team, to lead the process. This team includes people from the business units and information technology (IT). Information security is the responsibility of everyone in the organization, not just the IT department. People from the business units know what information is important to complete their tasks as well as how they access and use the information. The information technology staff understands issues related to computing infrastructure configuration as well as what is needed to keep it running. These perspectives are important in understanding the global, organizational view of information security risk. Below is a flow chart of how the INTEK Basic Security Services work.
desktop-integration-planning-lan/wan-security-procurement-warranty-web-wireless
The remote assessment components are performed from our facility against your Internet perimeter.
Network Scan
The scan provides a means for mapping the network and identifying which open ports exist on each host scanned. Part of the scan includes network mapping. Network mapping is performed by OS fingerprinting, which allows us to develop a rough idea of the network architecture. By identifying open ports, the types of services that are running on the systems can be determined, e.g. port 80 indicates the host is probably a web server. Using our toolset, we are sometimes able to determine what type and version the services are. This is especially critical in determining what approach a hacker would take, e.g. If a hacker determines IIS 5.0 is running would indicate Windows 2000 is installed, and from that the hacker would probably research known exploits and vulnerabilities that are specific to those systems/services. From a patch level perspective we can determine from the scan whether or not the TCP/IP patch has been installed for Win NT version. 4.0, and this is based on the TCP sequence number predictability.
Vulnerability Assessment
The vulnerability assessment feature runs a library of known vulnerabilities and exploits against the targeted systems. Depending on the responses to the scripted attacks, the program will report that the system is open to certain exploits. Reported vulnerabilities are only possible vulnerabilities. The assessment tool does not actually compromise the system but checks to see if conditions exist for a specific type of attack. Although when running DoS checks it could in fact bring the system down.
Assessment Results Reporting
A report will be provided that will explain the procedures and their results along with general recommendations on securing any vulnerabilities discovered. The reports will be presented in a well written, easy to understand format and will include the actual scan reports themselves for the more technically inclined people on the customer's IT staff.
Application Security Review
INTEK will review all web applications that use scripts to retrieve information from a database and display it via html to the end user. If these scripts are not written properly, hackers may be able to gain unauthorized access to sensitive data. INTEK will check targeted applications for the following programming practices, which if implemented correctly can help to prevent attacks from occurring. Encrypt stateless information if necessary. Using a randomly generated unique ID to track the user can prevent attacks, which are fairly easy, if static, sequenced IDs are used. Use session variables. Session variables are an advanced practice available in the latest web scripting languages, and track IDs and variables on the server side by tracking the user with a randomly generated ID. It is very secure, and prevents unauthorized entrance to a web site. Verify referring links. Though not foolproof, this ensures that traffic flows through a site as intended. It can also help spot malicious actions immediately. Program in checks to suppress standard error messages, which may reveal variables used in scripts, script names, and path names for the server.
Security Policies
Within organizations, the expanded use of connected computers to store, process, and share mission critical data has heightened the need to secure the network. Corporate networks are increasingly depending on the accessibility of their sensitive data from many different places, outside as well as inside the organization. This dependence requires very careful management of the technologies available to secure the data. The computer industry has developed many technologies to secure specific aspects of the storage and communication processes. These technologies are only as successful as the plan used to combine them. Security can be defined as "the state of being free from unacceptable risk". The risk concerns the following categories of losses:
The potential causes of these losses are termed "threats". These threats may be human or non-human, natural, accidental, or deliberate. Using vendor approved and international corporate standards, INTEK will work with the customer to develop a comprehensive policy of "best practices" and system configurations to reduce the chance of compromising information integrity or exposure via malicious or non-malicious means.
Server OS Patch Review
As part of the Server/Network operating system patch review, INTEK will scan all specified hosts and verify the latest service packs and hot fixes are correctly installed. Any deficiencies that are identified will be documented with recommended corrective actions. Optionally, INTEK consultants can supply and apply the needed patches.
Ongoing Security Maintenance
INTEK will provide the customer with the option of a security maintenance program that will allow the customer to stay focused on their business and at the same time know their systems and networks are secure and staying that way. The maintenance program will keep the customer up-to-date on the latest releases and developments in the security world as they relate to their configurations.
Patch Monitoring
As part of the maintenance program, INTEK will ensure that your systems will always have the latest service packs and hot fixes to keep your systems up-to-date. As updates are released or vulnerabilities posted, INTEK will provide the customer with this information as it comes out, tailored for their network/system configurations. The customer will have the option of updating systems themselves or have INTEK provide an engineer to perform this service for them.
Monthly Security News
An added feature to the maintenance subscription will be a monthly newsletter containing information on recent exploits and vulnerabilities, news on the latest and upcoming updates for system service packs and hot fixes, IT security trends and much more, keeping the customer update on happenings in the security world as it relates to them.
Quarterly Scan
Also as part of the maintenance subscription INTEK will conduct quarterly, monthly, weekly, or possibly daily scanning and vulnerability assessments based on your level of Risk, to ensure that system and network integrity is being maintained.
|